Owasp Zap API Scanning with Authentication From Desktop to Docker (Part 2)
Now we git clone the repository https://github.com/augmentonesecurity/oauth2_auth_resource_servers . Open 2 terminals and in each one, go into auth_server directory and resource_directory. Execute mvn spring-boot:run to start up both servers. When the resource server has started up, go to your browser and put in the url – http://127.0.0.1:8084/v2/api-docs . This points to the openapi spec in json. We will use this url to import into desktop Zap. Follow the instructions here – https://augment1security.com/api-scanning/how-to-import-openapi-swagger-api-specification-into-zap/
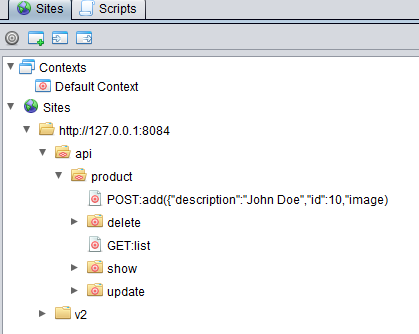
Once the openapi spec import is successful, you should see the Site tree being populated like below.
Now, let’s see if we can spider the api to test our the authentication script and httpsender script. We open up the Spider tab.
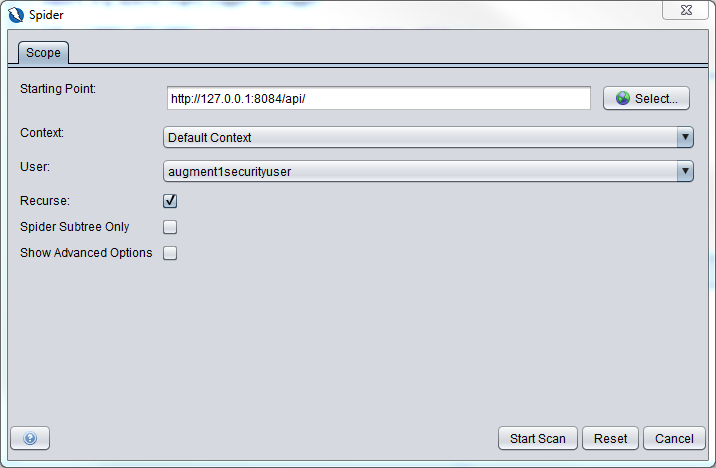
We click on the New Scan button, fill up the dialog box as shown below and click on the Start Scan button.
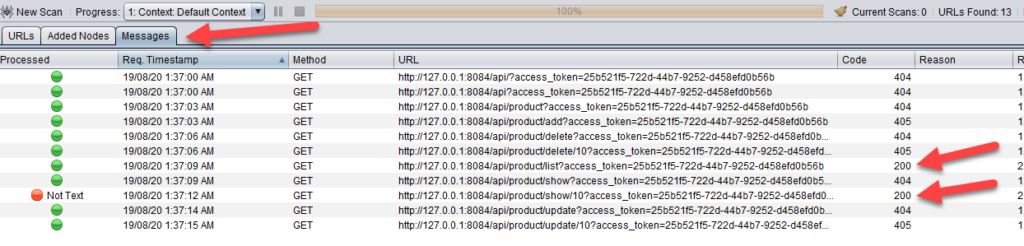
When you go to the Messages tab, you will see that there are urls which return back http status code 200. This means that the authentication is successful. You can also see that the access_token is appended to each url as a query parameter by the httpsender script – augment1security_accesstoken_setter.py.
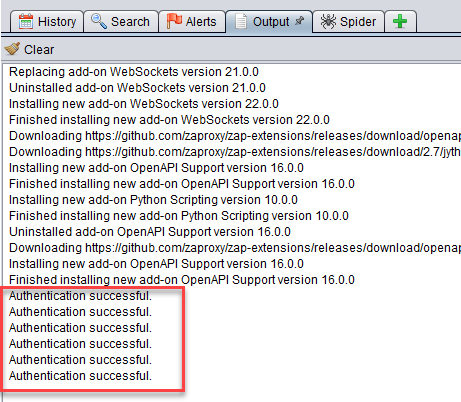
If you go to the Output tab, you can also see that authentication is successful.
Now we can “migrate” this to the dockerized Zap.
Got to Part 3